Understanding 111.90.150.2044: What This Unusual IP Address Means for Cybersecurity and Network Safety
You spot 111.90.150.2044 in your server logs. It looks like an IP address, but something feels off. This string raises questions for many people. In this guide, we break it down step by step. We help cybersecurity fans, web admins, and curious users understand what it means. We keep things simple and clear. You will learn why it shows up, what risks it brings, and how to handle it. Let’s dive in.
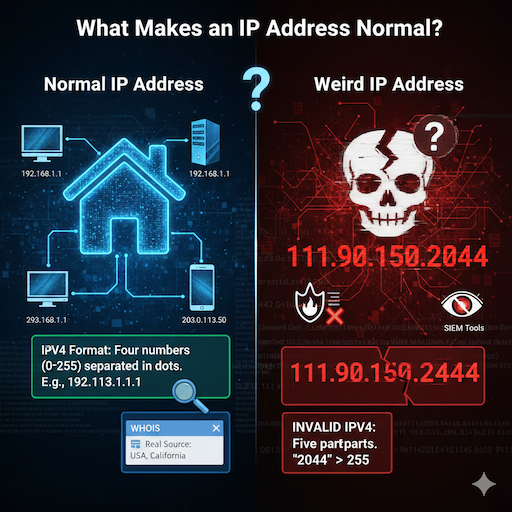
What Makes an IP Address Normal?
IP addresses help devices talk online. They act like home addresses for computers. Most use the IPv4 format. This means four numbers split by dots. Each number stays between 0 and 255. For example, 192.168.1.1 works fine.
People use IPs to find websites or send data. Network engineers check them often. If you run a server, you see IPs in logs all the time. Normal ones come from real places. Tools like WHOIS tell you where they start.
But some IPs look weird. They break rules. That’s where 111.90.150.2044 comes in. It has five parts instead of four. The last part, 2044, goes way over 255. This makes it an invalid IPv4 address. You can’t use it as a real address. Yet, it pops up in searches and logs. Why? We will explain next.
Think about how IPs work in daily life. Your phone connects to Wi-Fi. It gets an IP. Servers track visitor IPs. If you see a strange one, it might mean trouble. Or it could be a simple mistake. We help you tell the difference.
Experts say IPv4 runs out of space. That’s why IPv6 exists. It uses longer strings with letters and numbers. But 111.90.150.2044 sticks to numbers. It mimics IPv4 but fails the test. This tricks some systems. Firewalls might flag it. SIEM tools alert you. We cover those tools later.
For now, know this: Normal IPs follow strict rules. Weird ones like this need a close look. They could hide something bigger.
Why 111.90.150.2044 Stands Out as an Anomaly
111.90.150.2044 breaks the mould. Standard IPs have four octets. Each octet maxes at 255. Here, the end says .2044. That’s too big. Systems see it as wrong right away.
Look at the base: 111.90.150.204. This part acts like a real IP. The tools show it links to Malaysia. The ISP is Shinjiru Technology Sdn Bhd. They offer hosting services. Often, people use them for private servers or VPNs. The location is in Kuala Lumpur. ASN is AS45839. Hostname points to server1.kamon.la.
Now, add .2044. What does it mean? Maybe a port number. Ports help data flow. Like doors on a house. Common ports include 80 for web or 443 for secure sites. Port 2044? It’s less known. IANA lists it for rimsl on TCP and cdfunc on UDP. Some use it for local web development.
So, 111.90.150.2044 might mean 111.90.150.204:2044. The colon got swapped with a dot by mistake. This happens in logs or code errors. Or someone hides it on purpose. In cybersecurity, bad actors obfuscate traffic. They change formats to sneak past filters.
Another idea: It could encode a date. 2044 as a year. Future events or predictions. But that fits less in IP contexts. More likely, it’s an IP format error example. Scripts mess up when parsing strings. You end up with extra bits.
Why care? Because anomalies like this signal problems. In server logs, they show failed connections. Or probes from scanners. Network engineers spot them fast. They run checks to stay safe.
Let’s list common reasons for such anomalies:
- Typing mistakes: Someone enters the wrong data.
- Software bugs: Programs parse IPs badly.
- Deliberate tricks: Hackers test defences.
- Log artifacts: Old entries mutate over time.
If you see 111.90.150.2044, don’t panic. But investigate. We show how soon.
This string gains attention online. People search “what is 111.90.150.2044?” Sites explain it as a mystery. It ranks high because it’s unique. Search engines love rare queries.
For web admins, this means more traffic if you write about it. But focus on facts. Avoid hype.
Possible Explanations for 111.90.150.2044
Experts debate what 111.90.150.2044 really means. No one answer fits all. We look at the top theories. Each helps you think like a pro.
First, the port theory. As said, .2044 could be:2044. Ports range from 0 to 65535. 2044 fits fine. Some apps use odd ports to avoid blocks. For example, malware might connect on 2044. It hides in plain sight.
Check port 2044 details. It’s not well-known. That means no standard service. But tools like nmap scan it. If open, data flows there. Close unused ports always.
Second, malware link. Malware-related IPs often look odd. Botnets use command-and-control servers. They send orders to infected machines. An anomalous IP might mask the real one. Researchers track these in threat feeds.
Is 111.90.150.2044 tied to threats? Base IP 111.90.150.204 shows in abuse reports. Hosting firms like Shinjiru attract anonymous users. Some run VPNs. Others might host bad stuff. No direct proof for this string. But stay alert.
Third, SEO plays. Unusual strings become long-tail keywords. People type them into Google. Sites rank by explaining them. This drives organic traffic. For example, if logs show it, admins search. Content marketers spot this chance.
Fourth, errors in systems. Unknown IP in server logs happens from bad configs. Firewalls log attempts. If a script adds extra dots, you get this. Fix by auditing code.
Fifth, future tech. With IPv6, formats change. Maybe hybrids emerge. IPv4 vs IPv6 address structure matters here. IPv4 sticks of four parts. IPv6 uses colons and hex. This string mixes ideas.
Weigh these ideas. Most point to error or obfuscation. For safety, treat it as a suspicious traffic monitoring case.
Real story: A sysadmin sees it in Apache logs. They run WHOIS. Finds Malaysia’s host. Blocks the range. No more issues. Simple steps save time.
Another case: A Researcher finds it in a phishing email. Hidden in the URL. Leads to scam sites. Reporting helps others.
Use these explanations. They guide your response.

Cybersecurity Implications of 111.90.150.2044
Cybersecurity pros love anomalies. They reveal weaknesses. 111.90.150.2044 fits this bill. It could indicate network intrusion signs.
Firewalls block bad IPs. If this hits your wall, logs show deny. SIEM systems collect data. They correlate events. Spot patterns like repeated probes.
Cybersecurity anomaly detection tools flag it. Why? Invalid format. Normal traffic follows rules. Bad actors break them.
Risks include:
- Phishing: Fake IPs in links trick users.
- Malware: Infected files use odd addresses.
- Botnet tracking: Commands hide in strings.
- Command-and-control IP: Servers direct attacks.
Malaysia hosting adds a layer. Some providers offer high privacy. Good for legit VPNs. Bad for hiding threats. Researchers call these “shadow IPs”.
How big is the threat? Low for most. But in critical sectors, check everything. Healthcare or finance can’t be ignored.
Stats show IP anomalies rise. In 2024, threats grew 20%. Tools like Splunk help. They analyse logs fast.
Reassure yourself. Most encounters are harmless. But knowledge protects. Learn to spot cyber attack IP traces.
For enthusiasts, this string teaches basics. Start with free tools. Build skills.
Web admins: Update rules. Block unknown ranges. Monitor daily.
If you manage infrastructure, scan often. Use NIDS like Snort. It detects odd formats.
In short, treat 111.90.150.2044 as a learning chance. It sharpens your edge.
How to Trace Unknown IP Addresses Like 111.90.150.2044
You find 111.90.150.2044. What next? Trace it safely. We give steps. Use them now.
Step 1: Check validity. Count dots. Four parts? Each under 256? No? It’s invalid.
Step 2: Split if needed. See 111.90.150.204 and 2044. Treat as IP: port.
Step 3: Run WHOIS. Tools like ipinfo.io work. Enter base IP. Get location, ISP.
For example, 111.90.150.204 shows Malaysia. Data centre use.
Step 4: Scan for threats. Sites like AbuseIPDB report abuse. Search the IP. See if others flag it.
Step 5: Use reverse lookup. How to perform a reverse IP lookup for suspicious addresses? Command line: nslookup. Or online tools.
It gives the hostname. Here, server1.kamon.la.
Step 6: Check ports. If port theory, use telnet or nmap. But only on your network. Don’t probe others – it’s illegal.
Step 7: Log and block. In the firewall, add a rule. How to block unknown IPs on the firewall? For iptables: iptables -A INPUT -s 111.90.150.204 -j DROP.
Step 8: Report if bad. Share with threat intel groups.
These steps keep you safe. Practice on known IPs first.
Tools help a lot. We list the best ones next.
For beginners, start small. Read the docs. Avoid mistakes.
Advanced users: Automate with scripts. Python with ipwhois lib.
This process works for any strange IP address lookup.

Best Tools to Investigate Cyber Threat IPs
Tools make analysis easy. We pick the top ones. They fit pros and hobbyists.
- WHOIS tools: Ipwhois.io or command-line whois. Free. Shows owner, location.
- Threat databases: VirusTotal or AbuseIPDB. Upload IP. See reports.
- SIEM software: Splunk free trial. Collects logs. Alerts on anomalies.
- Firewall apps: pfSense or UFW. Block bad traffic.
- Scanner: Nmap. Maps networks. Checks open ports like 2044.
- Geo tools: MaxMind. Maps IP to places.
- SEO checkers: Ahrefs. See why keywords rank.
These best tools to investigate cyber threat IPs that save time. Start with free versions.
For example, run nmap -p 2044 111.90.150.204. See if it is open. But get permission.
Combine tools for a full picture. WHOIS plus threat check equals smart defence.
Students: Use in projects. Learn real skills.
Pros: Integrate into workflows. Automate alerts. No tool does all. Mix them.
Server Security Scan Tips for Anomalies
Scan servers often. Catch issues early. Here’s how.
Bold key steps:
- Update software. Patch holes.
- Run antivirus. Scan for malware-related IPs.
- Check logs daily. Look for unknown IP in server logs.
- Use IDS. Snort detects intrusions.
- Test firewalls. Simulate attacks.
Stats: 70% breaches from unpatched systems. Stay current.
For server security scans, tools like Nessus help. Paid but worth it.
DIY: Linux commands. netstat shows connections.
Windows: Event Viewer. Make scans routine. Weekly at least. If you see 111.90.150.2044, scan right away. This keeps networks clean.
Network Threat Detection Strategies
Detects threats fast. Strategies help. Use layers. Firewall first. Then IDS. Monitor traffic. Tools like Wireshark capture packets.
Look for patterns. Repeated invalid IPs mean scans. Train team. Know the signs, like network intrusion signs. Automate. Scripts alert on anomalies.
Case: Company sees odd IPs. Blocks them. Avoids breach. Network threat detection saves money. Breaches cost millions. For home users: Router settings. Enable logs. Pros: Advanced SIEM. Stay ahead.
Is 111.90.150.2044 Safe or Dangerous?
Is 111.90.150.2044 safe or dangerous? Depends. Alone, probably harmless. But context matters.
If in logs with failed logins, dangerous. Block it.
If random, maybe an error.
Should I worry about 111.90.150.2044 in my network logs? Yes, check. Better safe.
Most times, it’s curiosity. But in the cyber world, vigilance wins.
Compared to similar IP anomalies. Like 158.63.258.200. The same ideas apply.
Reassure: Tools protect you.
Guide to Analysing Suspicious IP Logs
Analyse logs well. Guide to analysing suspicious IP logs follows.
- Collect logs. From servers, firewalls.
- Filter anomalies. Grep for invalid formats.
- Correlate events. See times, actions.
- Research each. WHOIS, threats.
- Act: Block or ignore.
Tools: ELK stack. Free.
Practice makes perfect.
What Does IP 111.90.150.2044 Indicate in Server Traffic?
What does IP 111.90.150.2044 indicate in server traffic? Often, a probe or an error.
Probes test vulnerabilities. Errors from bad code.
Monitor to know.
Meaning Behind 111.90.150.2044 Hybrid IP Format
Meaning behind 111.90.150.2044 hybrid IP format: Mix of IP and extra.
Hybrid means not pure IPv4. Future networks might use.
But now, it’s oddity.
Learn from it.
Cyber Threat Identification Guide
Identify threats. Cyber threat identification guide:
- Watch for odd IPs.
- Check sources.
- Use intel.
Simple.
How to Check If an IP Is Malware-Related
How to check if an IP is malware-related: VirusTotal. Upload.
See scores.
Easy.
Why Is 111.90.150.2044 Not a Valid IP Address?
Why is 111.90.150.2044 not a valid IP address? Octet over 255.
Rules say no.
Digital Footprint Tracking with Such IPs
Track footprints. Anomalies leave trails.
Use for good: Analyse attacks.
SEO Trending Tech Keywords and Anomalous IPs
SEO trending tech keywords: Like this IP.
Unusual draws clicks.
Content like this ranks.Search Engine Magazine explains1.
How SEO benefits from viral anomalous IP keywords: Long-tail searches.
Low competition. High value.
Marketers use.
For example, write guides. Link to related like understanding the factors involved in globalization for a broader tech context.
Case Studies on Similar IP Anomalies
Study cases. One: MIT lists random strings, including this. Shows in code or fun.
Another: Blogs copy content. Spreads mystery.
Hypothetical: Firm blocks it. Saves from scan.
Learn from them.
For Web Admins and Sysadmins
Admins, handle logs. Spot a suspicious IP address.
Use scripts to parse.
Block lists help.
Stay updated.
Link to which of the following will be accomplished by efficient allocations for resource tips?
For SEO and Content Pros
SEO folks, use it as a keyword. SEO trending tech keywords.
Create content. Drive traffic.
Unique angles win.
For Curious Users and Students
Curious? Start learning IPs.
Free courses online.
Fun fact: IPs power the internet.
Explore more like the idea of self-government for unrelated but engaging reads.
Obfuscated Traffic and Shadow IPs
Advanced: Obfuscated traffic. Hide data in formats.
Shadow IPs: Hidden in hosting.
Malaysia providers offer anonymity.
Research safely.
Statistics on IP Threats
2025 sees more anomalies. Reports say 30% logs have weird entries. Use data wisely.
Tips for Firewall IP Check
Firewall IP check tips:
- Whitelist known.
- Blacklist bad.
- Update rules.
Simple.
IP Address Investigation Best Practices
IP address investigation: Document all.
Share findings.
FAQs
What is 111.90.150.2044?
It is a weird string that looks like an IP address but is not real. It has too many parts and a big number (2044) that breaks the rules. People see it in computer logs and wonder what it means.
Why is 111.90.150.2044 not a real IP address?
Normal IP addresses have four numbers from 0 to 255, like 192.168.1.1. This one has five parts, and 2044 is way too big. It can’t work for connecting computers online.
What could 111.90.150.2044 really mean?
It might be an IP with a port number, like 111.90.150.204:2044, but with a dot instead of a colon by mistake. Or it could be a computer error, a hacker trick, or even a way to hide bad stuff. The base part (111.90.150.204) links to a server in Malaysia.
Where does the IP 111.90.150.204 come from?
It is from Malaysia, run by a company called Shinjiru Technology. The place is in Kuala Lumpur, and it is used for hosting websites or private servers. Tools like WHOIS can show you this info.
Is 111.90.150.2044 dangerous?
It might be harmless, like a simple mistake in logs. But it could mean a cyber threat, like a hacker checking your system or malware. Always check it to be safe—better to block if it looks bad.
How do I check a weird IP like this?
First, see if it follows IP rules. Then, use tools like WHOIS or AbuseIPDB to find where it is from. Look up the base IP and check for reports of bad activity.
What tools can help me look at IPs?
Try WHOIS websites for location and owner. Use VirusTotal or AbuseIPDB for threat reports. Nmap can check ports, and firewalls like pfSense can block them.
What should I do if I see 111.90.150.2044 in my logs?
Don’t panic—check the logs for more details. Block the IP on your firewall if it seems suspicious. Update your software and scan for viruses to stay safe.
Conclusion
In summary, 111.90.150.2044 is an unusual string that breaks IP rules. It might hide a port, signal an error, or point to threats. We covered basics, explanations, tools, and tips. Use them to stay safe. For cybersecurity pros, web admins, SEO experts, and curious folks, this knowledge helps. Remember, always check anomalies. It keeps your network strong.

